LWO CRYPT
A certified cryptographic information protection tool
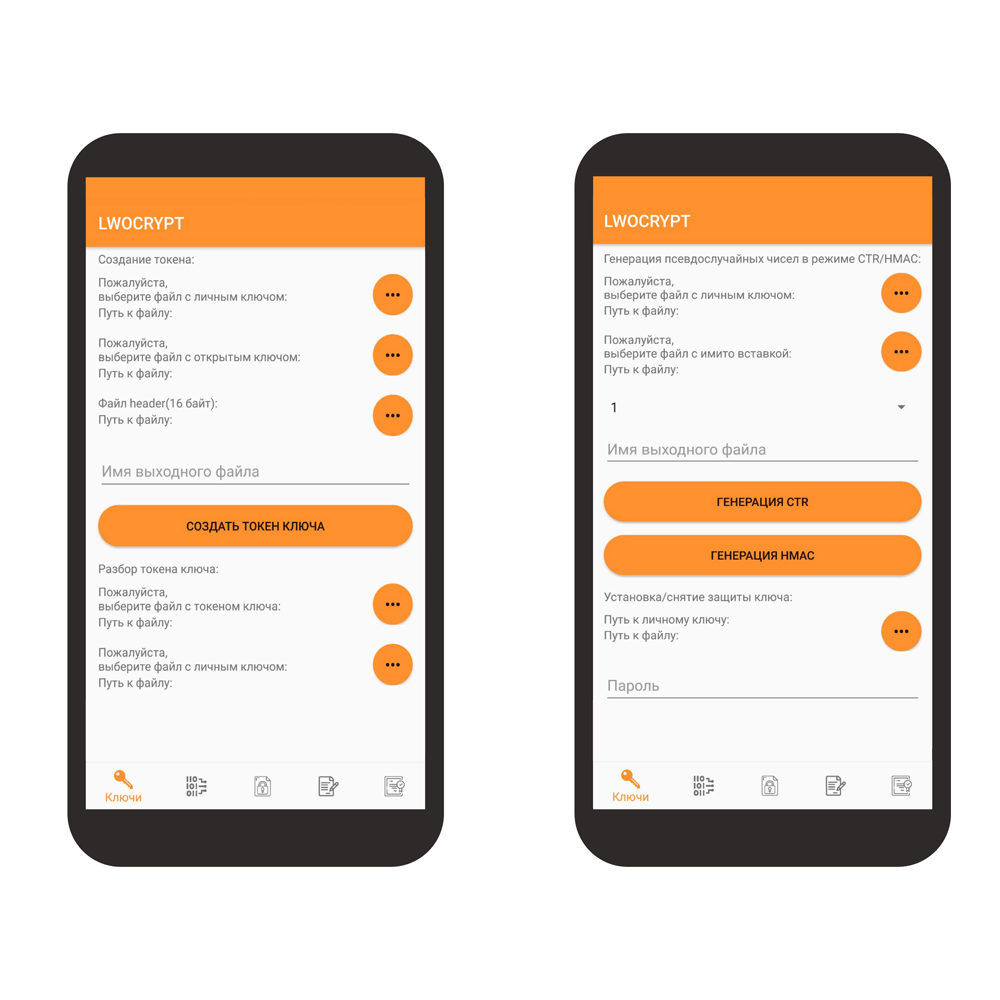
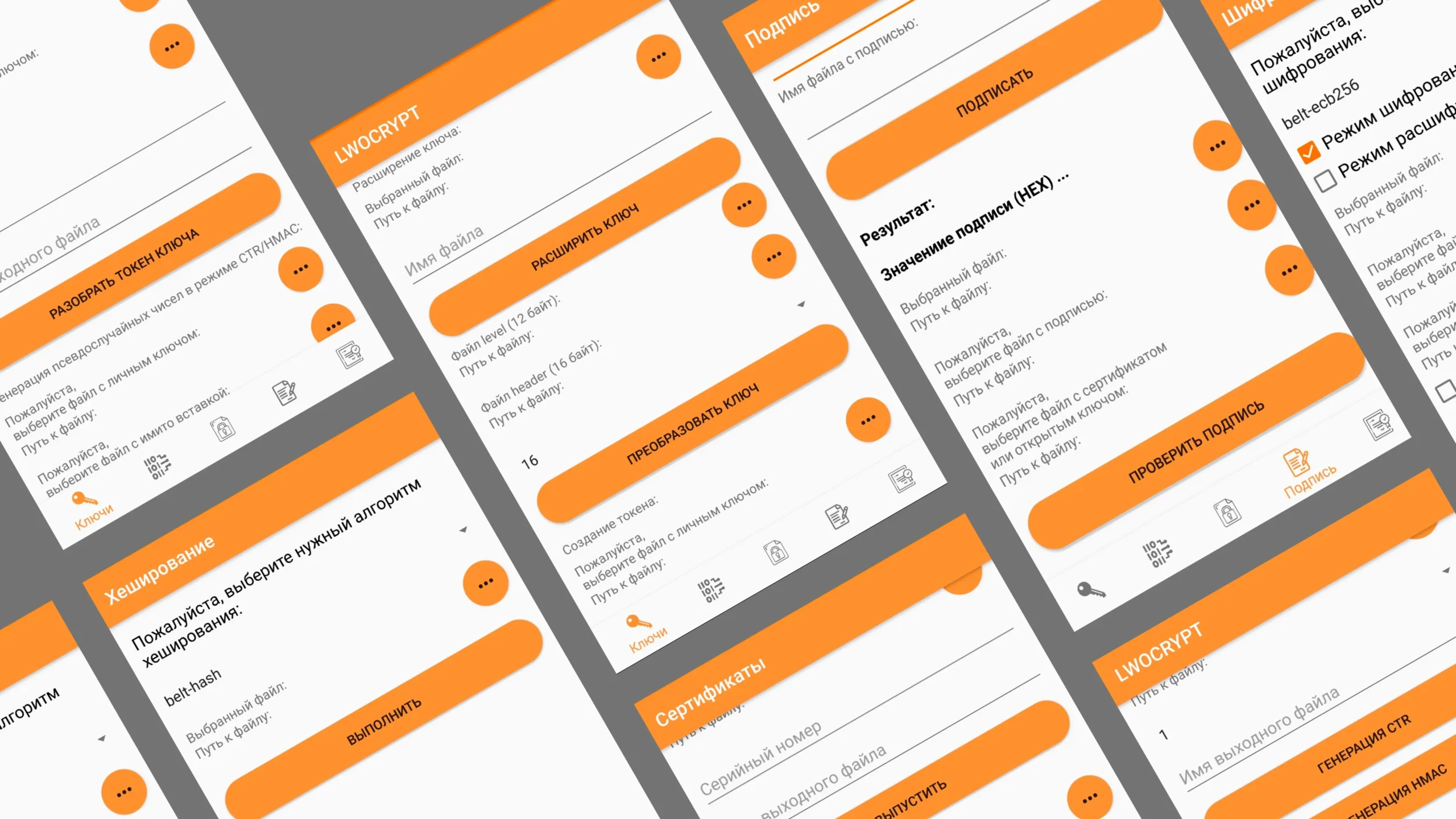
Functional capabilities of the system:
- Generating a certificate request
- Verification of the certification path
- Use of cryptographic message syntax
- Online certificate status check
- Data encryption, HMAC generation, authenticated data encryption, hashing, key expansion, key transformation
- Key pair generation and verification, one-time private key generation, digital signature generation and verification, key transport, private key password protection, use of standard elliptic curve parameter sets, use of Abstract Syntax Notation One module
- HMAC generation in HMAC mode, pseudo-random number generation in counter mode and HMAC mode
- Establishing the transport (communication) level security protocol
- Hashing
- Generating a request for obtaining a certificate, public key certificate, certificate revocation list, signed data, enveloped data, OCSP request and response, and establishing an application programming interface
The main purpose of the system:
System Advantages:
LWO CRYPT provides:
Security
LWO Crypt ensures the confidentiality, authenticity, and integrity of data. The software architecture allows using a file-protected key container as a key storage
Functionality
Thanks to the dynamically linked libraries included in LWO Crypt, cryptographic services can easily be invoked from any developed product for server infrastructures, desktop, and mobile applications
Flexibility
To perform cryptographic operations on files, LWO Crypt can be launched via a command-line console
Compatibility
LWO Crypt provides software wrappers that enable easy integration with Java applications, NodeJS servers (with a ready-made npm package). There is also a software wrapper in the form of a network microservice, allowing interaction with LWO Crypt using HTTP requests in the REST API architecture, including the ability to interact from any web browser
Android Compatibility
Integration with Android applications is ensured through the presence of an “Android Library Project” binary distribution in LWO Crypt, available as an .aar library
iOS Compatibility
Integration with iOS applications is enabled through the availability of a binary framework in LWO Crypt, provided as a library with easy integration into Swift and other applications
Want to discuss a joint project?
Be our partner and together we will achieve your expectations